Prove your systems are secure and compliant, or get them to that level fast
Prove your systems are secure and compliant, or get them to that level fast
Prove your systems are secure and compliant, or get them to that level fast
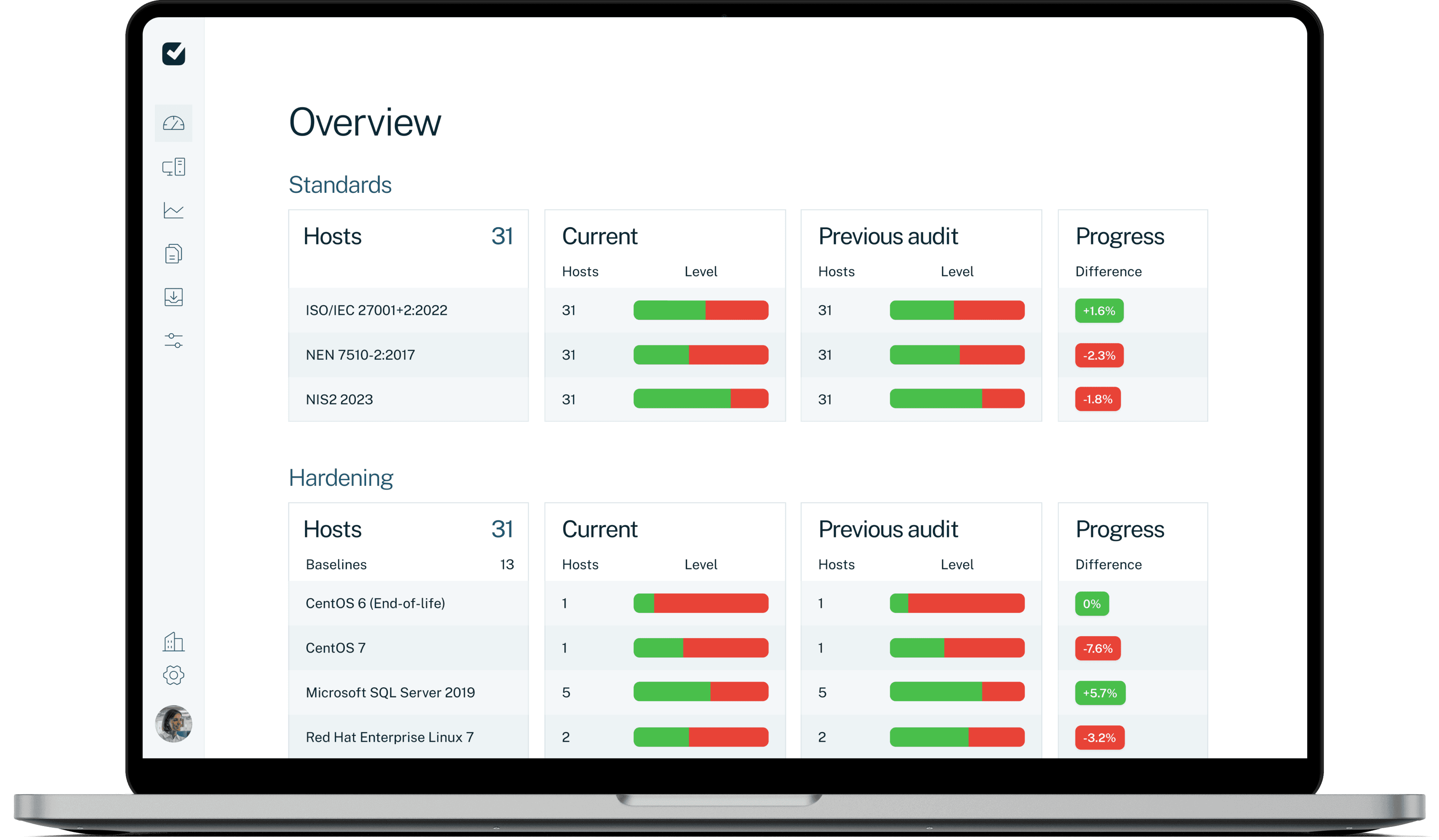
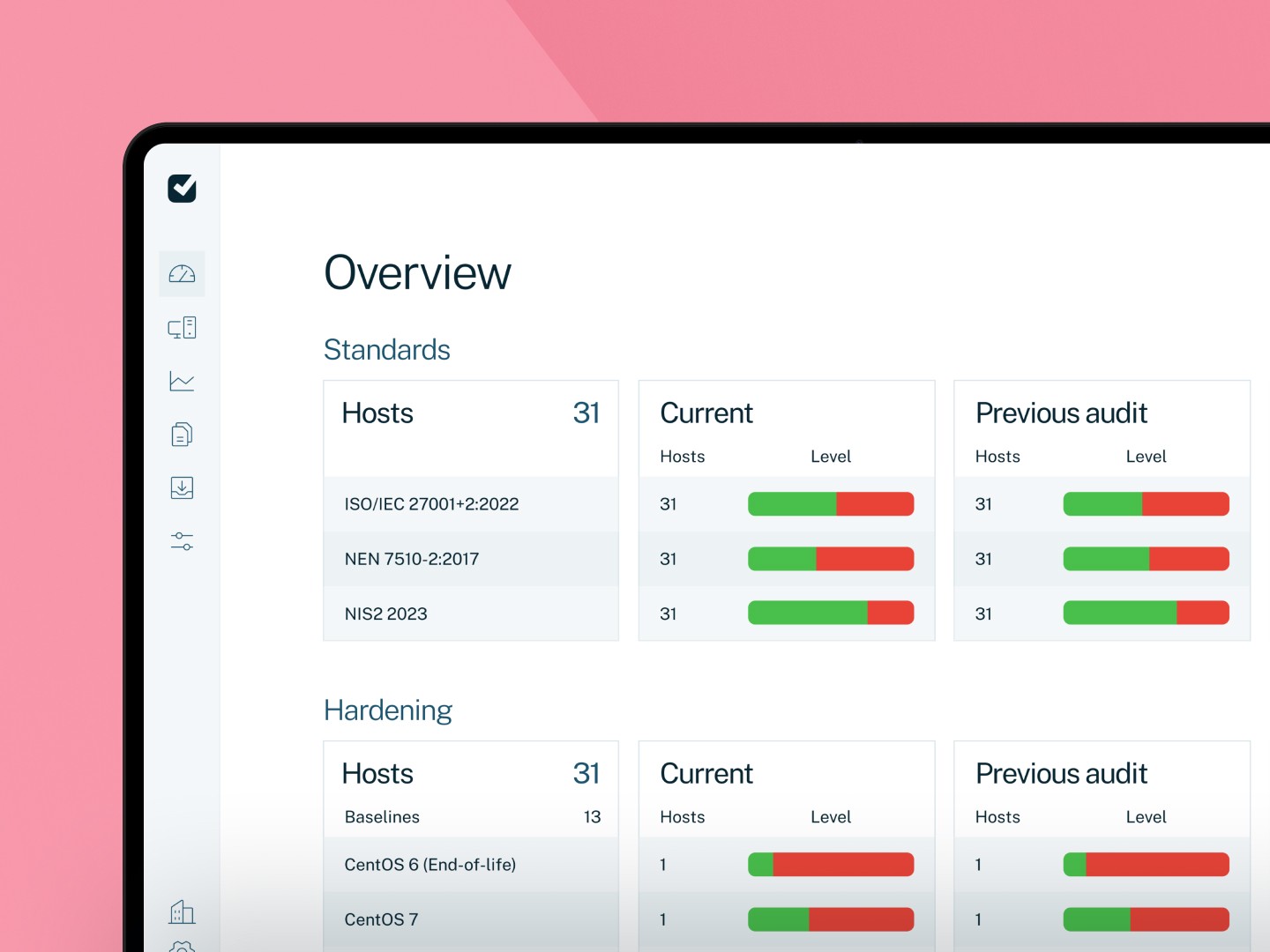
Easy2audit checks users and systems against frameworks such as NIS2,
ISO 27001/2, BIO, NEN7510 and DORA.
Our solution shows where configurations deviate and helps close digital doors and windows in a targeted, measurable way.
Easy2audit checks users and systems against frameworks such as NIS2,
ISO 27001/2, BIO, NEN7510 and DORA.
Our solution shows where configurations deviate and helps close digital doors and windows in a targeted, measurable way.
Easy2audit checks users and systems against frameworks such as NIS2,
ISO 27001/2, BIO, NEN7510 and DORA.
Our solution shows where configurations deviate and helps close digital doors and windows in a targeted, measurable way.
On average,
90% faster from finding to report.
Unique software solution that audits and remediates.
Cloud or on-premise?
Your choice
Security and compliance you can demonstrate




Easy2audit is
Built for professionals who must prove security and compliance
Easy2Audit supports roles where decisions must be defensible, repeatable, and audit-ready — across compliance, security, and IT operations.
IT & Security
For IT teams, security officers and MSP's that want to lock down their digital doors and windows.
Shorten hardening projects from years to weeks.
85 -95% less effort with production tested baselines.
Continuous overview of misconfigurations.
Explore IT & Security
➔
Audit & Compliance
For auditors, accountants, and organisations that must reliably prove compliance and security.
Reproducible results
Quick answers to NIS2, ISO 27001/2, BIO, DORA and CIS questions
Reduce audit effort by up to 90%
Explore audit & compliance
➔
Easy2audit is
Built for professionals who must prove security and compliance
Easy2Audit supports roles where decisions must be defensible, repeatable, and audit-ready — across compliance, security, and IT operations.

IT & Security
For IT teams, security officers and MSP's that want to lock down their digital doors and windows.
Shorten hardening projects from years to weeks.
85 -95% less effort with production tested baselines.
Continuous overview of misconfigurations.
Explore IT & Security
➔

Audit & Compliance
For auditors, accountants, and organisations that must reliably prove compliance and security.
Reproducible results
Quick answers to NIS2, ISO 27001/2, BIO, DORA and CIS questions
Reduce audit effort by up to 90%
Explore audit & compliance
➔
Easy2audit is
Built for professionals who must prove security and compliance
Easy2Audit supports roles where decisions must be defensible, repeatable, and audit-ready — across compliance, security, and IT operations.

IT & Security
For IT teams, security officers and MSP's that want to lock down their digital doors and windows.
Shorten hardening projects from years to weeks.
85 -95% less effort with production tested baselines.
Continuous overview of misconfigurations.
Explore IT & Security
➔

Audit & Compliance
For auditors, accountants, and organisations that must reliably prove compliance and security.
Reproducible results
Quick answers to NIS2, ISO 27001/2, BIO, DORA and CIS questions
Reduce audit effort by up to 90%
Explore audit & compliance
➔
Why compliance and hardening are urgent
Regulators, supply-chain partners, and cyber insurers increasingly demand demonstrable proof that IT systems are securely configured.
With frameworks like NIS2, DORA, and ISO 27001:2022, “we think it’s secure” is no longer sufficient.
Traditional audit methods don’t scale
Quickly acquire valuable information with detailed IT reports and a user-friendly dashboard tailored to your needs.


Traditional audit methods don’t scale
Quickly acquire valuable information with detailed IT reports and a user-friendly dashboard tailored to your needs.


Traditional audit methods don’t scale
Quickly acquire valuable information with detailed IT reports and a user-friendly dashboard tailored to your needs.


Easily identify vulnerabilities
Uncover system vulnerabilities to inform data-driven decisions.
percent of administrator accounts are inactive.
Easily identify vulnerabilities
Uncover system vulnerabilities to inform data-driven decisions.
percent of administrator accounts are inactive.
Easily identify vulnerabilities
Uncover system vulnerabilities to inform data-driven decisions.
percent of administrator accounts are inactive.
Scale audits without compromise
Evaluate passwords, accounts, and access across one system or thousands—quickly and accurately.
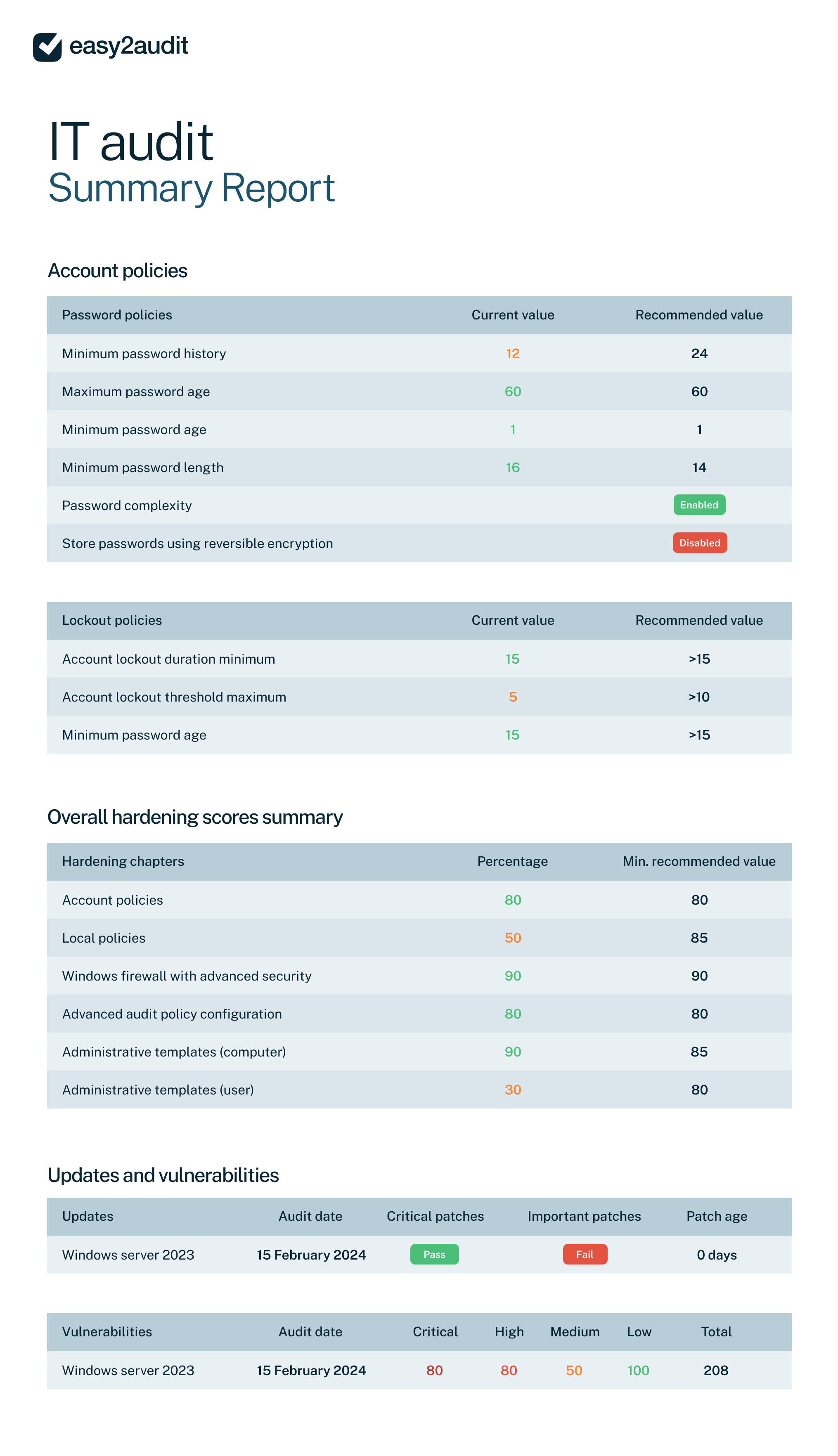
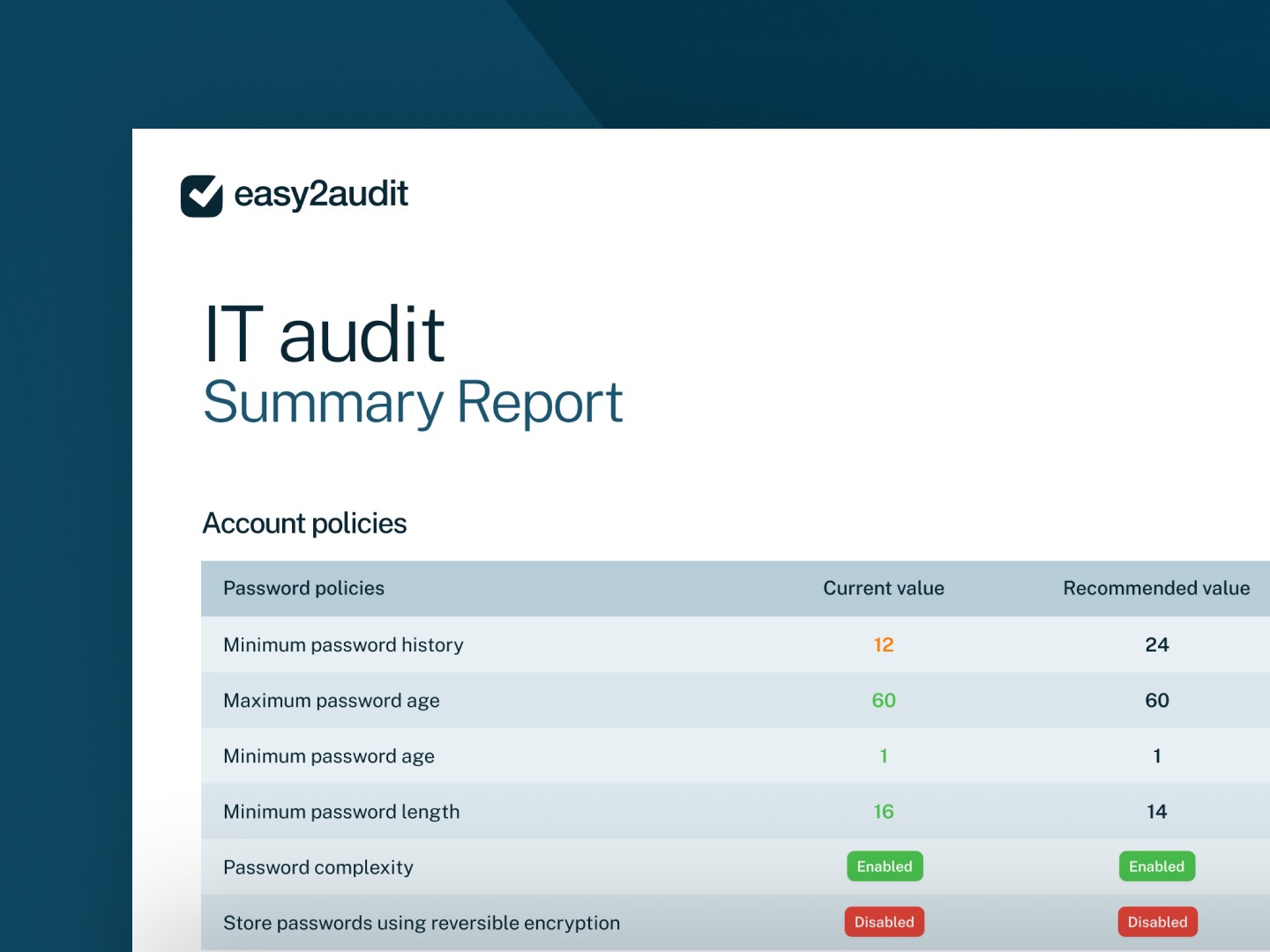
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Scale audits without compromise
Evaluate passwords, accounts, and access across one system or thousands—quickly and accurately.
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Scale audits without compromise
Evaluate passwords, accounts, and access across one system or thousands—quickly and accurately.
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Minimum password history
User characteristics
Login type
Account policies
Password policies
Total users
SQL Login: Enabled
Not restricted to specific workstation
Enforce Password history is set to 24
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Maximum password age is set to 365
SQL version value
Active users
Maximum password age
Minimum password age is set to 1
Listing of Wox permissions on the DB
Inactive users
Minimum password age
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Password complexity
Administrator rights
Listing of accounts last login dates
Minimum password length is set to 14 or more characters
Store passwords using reversible encryption
Domain administrator
Number of logins last year
Windows firewall with advanced security
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Number of logins YTD
Default DB
Password not required to logon
Administrative templates (computer)
Server role: Public
Login mode: Integrated
No home directory
Store passwords using reversible encryption
Traditional Hardening timelines are no longer acceptable
Hardening an average environment to a solid baseline (e.g. CIS Level 1) typically takes around two years.
Understaffed teams and constant firefighting cause projects to stall, costs to rise, and critical measures to remain unimplemented.
Audits and hardening both depend heavily on scarce expertise and time.
Easy2Audit compresses both — dramatically.
Hardening
Authorisations
Patching
Vulnerabilities
Traditional Hardening timelines are no longer acceptable
Hardening an average environment to a solid baseline (e.g. CIS Level 1) typically takes around two years.
Understaffed teams and constant firefighting cause projects to stall, costs to rise, and critical measures to remain unimplemented.
Audits and hardening both depend heavily on scarce expertise and time.
Easy2Audit compresses both — dramatically.
Hardening
Authorisations
Patching
Vulnerabilities
Traditional Hardening timelines are no longer acceptable
Hardening an average environment to a solid baseline (e.g. CIS Level 1) typically takes around two years.
Understaffed teams and constant firefighting cause projects to stall, costs to rise, and critical measures to remain unimplemented.
Audits and hardening both depend heavily on scarce expertise and time.
Easy2Audit compresses both — dramatically.
Hardening
Authorisations
Patching
Vulnerabilities
The Risk
Legal Liability
A Dutch law case
shows that IT administrators without basic hardening can be held legally liable. In a recent case, an IT provider without MFA was ordered to pay €864,000 in damages — not covered by insurance.

Supply-chain responsibility adds pressure
Clients increasingly verify whether their suppliers are demonstrably secure.
Easy2audit has extensive international experience across sectors.
References from accounting firms, government bodies, and MSPs are available on request.

The Risk
Legal Liability
A Dutch law case
shows that IT administrators without basic hardening can be held legally liable. In a recent case, an IT provider without MFA was ordered to pay €864,000 in damages — not covered by insurance.

Supply-chain responsibility adds pressure
Clients increasingly verify whether their suppliers are demonstrably secure.
Easy2audit has extensive international experience across sectors.
References from accounting firms, government bodies, and MSPs are available on request.

The Risk
Legal Liability
A Dutch law case
shows that IT administrators without basic hardening can be held legally liable. In a recent case, an IT provider without MFA was ordered to pay €864,000 in damages — not covered by insurance.

Supply-chain responsibility adds pressure
Clients increasingly verify whether their suppliers are demonstrably secure.
Easy2audit has extensive international experience across sectors.
References from accounting firms, government bodies, and MSPs are available on request.

Our Step by Step Process
From audit to demonstrably more secure
A structured, reproducible process that turns audit findings into measurable security improvement.
1. Audit your systems
Easy2audit scans servers, workstations, and other systems against NIS2, ISO 27001/2, BIO, NEN 7510, DORA, and CIS Benchmarks.
You see which security settings, user privileges, antivirus status, and patches apply — and where deviations exist.
2. Get immediately actionable insights
Results appear in clear dashboards and audit-ready reports suitable for audits, financial statements, and management accountability.
Findings are traceable to concrete systems and configurations — no black-box interpretation.
3. Accelerate hardening
IT or Security teams act on findings using production-tested baselines.
A traditional hardening project drops from ~2 years to ~6 weeks, with maximum risk reduction.
Our Step by Step Process
From audit to demonstrably more secure
A structured, reproducible process that turns audit findings into measurable security improvement.
1. Audit your systems
Easy2audit scans servers, workstations, and other systems against NIS2, ISO 27001/2, BIO, NEN 7510, DORA, and CIS Benchmarks.
You see which security settings, user privileges, antivirus status, and patches apply — and where deviations exist.
2. Get immediately actionable insights
Results appear in clear dashboards and audit-ready reports suitable for audits, financial statements, and management accountability.
Findings are traceable to concrete systems and configurations — no black-box interpretation.
3. Accelerate hardening
IT or Security teams act on findings using production-tested baselines.
A traditional hardening project drops from ~2 years to ~6 weeks, with maximum risk reduction.
Our Step by Step Process
From audit to demonstrably more secure
A structured, reproducible process that turns audit findings into measurable security improvement.
1. Audit your systems
Easy2audit scans servers, workstations, and other systems against NIS2, ISO 27001/2, BIO, NEN 7510, DORA, and CIS Benchmarks.
You see which security settings, user privileges, antivirus status, and patches apply — and where deviations exist.
2. Get immediately actionable insights
Results appear in clear dashboards and audit-ready reports suitable for audits, financial statements, and management accountability.
Findings are traceable to concrete systems and configurations — no black-box interpretation.
3. Accelerate hardening
IT or Security teams act on findings using production-tested baselines.
A traditional hardening project drops from ~2 years to ~6 weeks, with maximum risk reduction.
TRANSPARENT.
REPRODUCIBLE.
AUDIT-PROOF.
Clear measurements, consistent methods, and results you can verify — every time.
Auditors can verify
Auditors see exactly the same data — no black boxes.
Reproducible results
Same scan, same standards, same output — every time.
Facts, not interpretations
Decisions based on validated data, not gut feeling.
On-premises supported
Sensitive environments stay local if required.
Fast reporting
What took weeks is reported in minutes.
Multiple frameworks at once
NIS2, ISO 27001, BIO, CIS — mapped automatically.
TRANSPARENT.
REPRODUCIBLE.
AUDIT-PROOF.
Clear measurements, consistent methods, and results you can verify — every time.
Auditors can verify
Auditors see exactly the same data — no black boxes.
Reproducible results
Same scan, same standards, same output — every time.
Facts, not interpretations
Decisions based on validated data, not gut feeling.
On-premises supported
Sensitive environments stay local if required.
Fast reporting
What took weeks is reported in minutes.
Multiple frameworks at once
NIS2, ISO 27001, BIO, CIS — mapped automatically.
TRANSPARENT.
REPRODUCIBLE.
AUDIT-PROOF.
Clear measurements, consistent methods, and results you can verify — every time.
Auditors can verify
Auditors see exactly the same data — no black boxes.
Reproducible results
Same scan, same standards, same output — every time.
Facts, not interpretations
Decisions based on validated data, not gut feeling.
On-premises supported
Sensitive environments stay local if required.
Fast reporting
What took weeks is reported in minutes.
Multiple frameworks at once
NIS2, ISO 27001, BIO, CIS — mapped automatically.
Choose what fits your situation
Easy2audit has extensive international experience across all sectors.
References from, for example, accounting firms, government bodies or MSPs are available on request.
Reproducible audits, without debate
Manual evidence from spreadsheets or screenshots, Easy2Audit delivers reproducible measurements mapped to compliance frameworks — you validate the scan, not interpretation.
From uncertainty to provable security
Manual checks don't scale across modern IT environments or security requirements. Easy2Audit shows where systems deviate from NIS2, ISO 27001, or CIS — and which issues should be prioritised.
Scale compliance without complexity
Manual audits don't scale across clients with different compliance requirements. Easy2Audit automates audits using one consistent method — with scalable reporting across all customers.
Evidence, not assurances
NIS2 requires demonstrable proof of secure system configuration. Easy2Audit shows — technically and reproducibly — where your organisation stands against NIS2 requirements.
Choose what fits your situation
Easy2audit has extensive international experience across all sectors.
References from, for example, accounting firms, government bodies or MSPs are available on request.
Reproducible audits. No debate.
Stop relying on spreadsheets, screenshots, or manual reports that are hard to verify. Easy2Audit delivers reproducible measurements mapped directly to compliance frameworks — you validate the scan, not someone's interpretation.
Prove security, not assumptions.
Manual checks don't scale. Easy2Audit shows where systems deviate from NIS2, ISO 27001, or CIS — and what to prioritise.
Choose what fits your situation
Easy2audit has extensive international experience across all sectors.
References from, for example, accounting firms, government bodies or MSPs are available on request.
Reproducible audits. No debate.
Stop relying on spreadsheets, screenshots, or manual reports that are hard to verify. Easy2Audit delivers reproducible measurements mapped directly to compliance frameworks — you validate the scan, not someone's interpretation.
Prove security, not assumptions.
Manual checks don't scale. Easy2Audit shows where systems deviate from NIS2, ISO 27001, or CIS — and what to prioritise.
From findings to defensible action — faster and more effective
Easy2audit helps organizations gain insight faster, set better priorities and demonstrably underpin decisions towards management, customers and auditors.
0%
Faster from finding to reporting
0%
Less time spent on system audits
0 weeks
Previous duration - 2 years
~0%
Decreased effort for hardening projects
From findings to defensible action — faster and more effective
Easy2audit helps organizations gain insight faster, set better priorities and demonstrably underpin decisions towards management, customers and auditors.
0%
Faster from finding to reporting
0%
Less time spent on system audits
0 weeks
Previous duration - 2 years
~0%
Decreased effort for hardening projects
From findings to defensible action — faster and more effective
Easy2audit helps organizations gain insight faster, set better priorities and demonstrably underpin decisions towards management, customers and auditors.
0%
Faster from finding to reporting
0%
Less time spent on system audits
0 weeks
Previous duration - 2 years
~0%
Decreased effort for hardening projects
The Return on Investment is clear.
For a fraction of the cost, you become compliant, hardened, and audit-ready.
Manual
Current Situation
1,000+ audit hours per year
€100k+ internal cost
External auditors: €15–20k
Hardening: ~2 years
Higher breach risk and liability
Easy2audit
Popular
Optimised Situation
90% faster audits
~8 hours per year
~€100k annual savings
Hardening in ~6 weeks
80–90% risk reduction
The Return on Investment is clear.
For a fraction of the cost, you become compliant, hardened, and audit-ready.
Manual
Current Situation
1,000+ audit hours per year
€100k+ internal cost
External auditors: €15–20k
Hardening: ~2 years
Higher breach risk and liability
Easy2audit
Popular
Optimised Situation
90% faster audits
~8 hours per year
~€100k annual savings
Hardening in ~6 weeks
80–90% risk reduction
With us, it is not a long story
Efficient IT audits, built for scale
Efficient IT audits, built for scale
Easy2audit reduces the operational burden of audits while improving quality and consistency.
8 hours
saved per system
8 hours
saved per system
8 hours
saved per system
1 source
of truth
1 source
of truth
1 source
of truth
Teams benefit from:
Teams benefit from:
Faster audit cycles
Less manual administration
Clear accountability and follow-up
Improved audit quality across the organisation
The result: audits that support decision-making instead of slowing it down.
The result: audits that support decision-making instead of slowing it down.
96% score on account policies.
96% score on account policies.
96% score on account policies.



Compliance & Regulations
FRAMEWORK-AGNOSTIC. TECHNICALLY PRECISE.
Easy2Audit maps technical configurations against what frameworks actually require — not what policies claim.
NEN 7510
CIS
DORA
NIS2
ISO 27002
BIO / BIO2
Compliance & Regulations
FRAMEWORK-AGNOSTIC. TECHNICALLY PRECISE.
Easy2Audit maps technical configurations against what frameworks actually require — not what policies claim.
NEN 7510
CIS
DORA
NIS2
ISO 27002
BIO / BIO2
Compliance & Regulations
FRAMEWORK-AGNOSTIC. TECHNICALLY PRECISE.
Easy2Audit maps technical configurations against what frameworks actually require — not what policies claim.
NIS2
ISO 27002
NIST
ISA 315
CIS v8
What professionals say about Easy2audit
What professionals say about Easy2audit
Trusted by organisations that value clarity, structure, and reliable audit outcomes.
Trusted by organisations that value clarity, structure, and reliable audit outcomes.
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
Resources
The latest insights
Discover the latest industry news, interviews, and other insightful content.
The Return on Investment is clear.
For a fraction of the cost, you become compliant, hardened, and audit-ready.
Manual
Current Situation
1,000+ audit hours per year
€100k+ internal cost
External auditors: €15–20k
Hardening: ~2 years
Higher breach risk and liability
Easy2audit
Popular
Optimised Situation
90% faster audits
~8 hours per year
~€100k annual savings
Hardening in ~6 weeks
80–90% risk reduction
The Return on Investment is clear.
For a fraction of the cost, you become compliant, hardened, and audit-ready.
Manual
Current Situation
1,000+ audit hours per year
€100k+ internal cost
External auditors: €15–20k
Hardening: ~2 years
Higher breach risk and liability
Easy2audit
Popular
Optimised Situation
90% faster audits
~8 hours per year
~€100k annual savings
Hardening in ~6 weeks
80–90% risk reduction









